如何使用 C# 解密使用 RSA1024 加密的 MD5 哈希值
我在工作中试图验证文件的完整性,但遇到了困难。我不太熟悉加密和散列,所以请耐心等待。
我有一些文件末尾有 MD5 哈希值。我编写了代码来获取我认为是哈希值的字节,并且它们的长度统一为 128 字节。在文件中,哈希值之前是关键字“RSA1024”,我认为该哈希值是使用 RSA 1024 加密的。
我知道文件中存在 RSA 密钥,并且已读出字节(始终为 258 字节长)。我看过很多使用 FromXmlString() 提取密钥的教程,但这个 RSA 密钥不是使用 .net 框架生成的,也不是 XML 格式。
我编写了以下方法来使用密钥解密哈希数据,并且在执行 ImportCspBlob() 时抛出此错误 - System.Security.Cryptography.CryptographicException:提供程序的错误版本。
有什么想法吗?
public byte[] DecryptRSA(byte[] encryptedData, byte[] keyData)
{
CspParameters param = new CspParameters();
param.Flags = CspProviderFlags.UseExistingKey;
RSACryptoServiceProvider rsaProvider = new RSACryptoServiceProvider(param);
rsaProvider.ImportCspBlob(keyData);
byte[] decryptedData = rsaProvider.Decrypt(encryptedData, false);
return decryptedData;
}
基本算法
想要“解密 MD5 哈希”可能听起来很奇怪,尤其是当有人说他们想要“用公钥解密”时。但这就是数字签名的工作原理。使用 RSA,您可以:
- 使用私钥加密
- 使用公钥解密
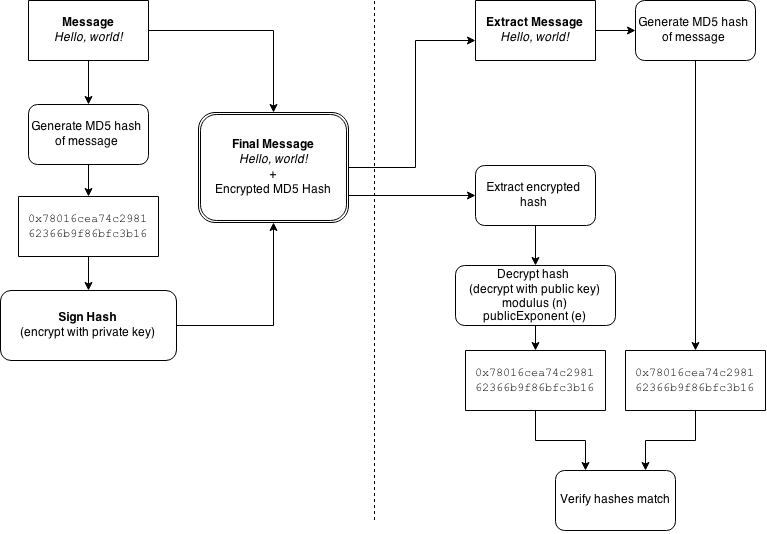
消息摘要使用私钥加密,并且只能使用公钥解密。这样您就知道只有拥有私钥的人才能签署该消息。
I trying to verify the integrity of a file at work and an having a hard time of it. I'm not very well versed with encryption and hashing, so bear with me.
I have some files that have an MD5 hash located at the end of them. I have written code to grab the bytes that I think are the hash and they seen to be uniformly 128 bytes long. In the file, just before the hash, is the keyword "RSA1024", which I have taken to mean the hash is encrypted using RSA 1024.
I have what I know is the RSA key in a file, and have read out the bytes (always 258 bytes long). I have seen many tutorials which use FromXmlString() to pull in the key, but this RSA key was not generated using the .net framework, and is not in an XML format.
I have written the following method to decrypt the hash data using the key, and it throws this error when executing ImportCspBlob() - System.Security.Cryptography.CryptographicException: Bad Version of provider.
Any ideas?
public byte[] DecryptRSA(byte[] encryptedData, byte[] keyData)
{
CspParameters param = new CspParameters();
param.Flags = CspProviderFlags.UseExistingKey;
RSACryptoServiceProvider rsaProvider = new RSACryptoServiceProvider(param);
rsaProvider.ImportCspBlob(keyData);
byte[] decryptedData = rsaProvider.Decrypt(encryptedData, false);
return decryptedData;
}
Basic Algorithm
It may sound strange to want to "decrypt an MD5 hash", and especially when one says that they want to "decrypt it with a public key". But that is how digital signatures work. With RSA you can:
- encrypt with private key
- decrypt with the public key

The message digest is encrypted with the private key, and can then only be decrypted with the public key. That way you know that only the person with the private key could have signed the message.
如果你对这篇内容有疑问,欢迎到本站社区发帖提问 参与讨论,获取更多帮助,或者扫码二维码加入 Web 技术交流群。

绑定邮箱获取回复消息
由于您还没有绑定你的真实邮箱,如果其他用户或者作者回复了您的评论,将不能在第一时间通知您!

发布评论
评论(2)
您的密钥很可能不是 CSP 类型的密钥(很可能是 DER 编码的)。您可以使用 Bouncy Castle 和 DER 密钥对其进行解密,如下所示:
编辑: 解决可能是签名验证操作的 GregS 场景
如果您尝试验证签名,则需要用于验证消息的证书、原始消息文本以及要进行比较的现有消息签名。
您要做的就是传入原始消息文本(减去签名)、消息签名的字节以及用于验证传入签名的证书的路径。
然后,您将对原始消息进行哈希处理,并将结果与传入的签名进行比较。
下面是一些代码来说明:
Your key is most likely not a CSP-type key (it is most likely DER encoded). You can decrypt it using Bouncy Castle with the DER key like this:
EDIT: to addressing GregS scenario that it may be a signature verify operation
If you are trying to verify a signature, you would need a certificate used to verify a message, the original message text, and the existing message signature to compare against.
What you do is pass in the original message text (minus the signature), the bytes of the message signature, and the path to the certificate you will use to verify the passed in signature.
Then, you will hash the original message and compare the result against the passed in signature.
Here is some code to illustrate:
MD5 是单向哈希。但你可以检查一下哈希算法。有一些方法可以破解这个哈希值,只需做一些研究即可;)
MD5 is one-way hash. But you might check out hashing algorithm. There are some ways to break this hash, just do some research ;)