md5sum 包含总和本身的文件?
我用 C++ 编写了一个由单个 EXE 文件组成的小应用程序。
我想将可执行文件本身的 md5sum 放入其“关于”对话框中。它应该静态嵌入到可执行文件中(以便可以从十六进制编辑器中看到),而不是动态计算。
I have written a small app in C++ consisting of a single EXE file.
I want to put in its "about" dialog the md5sum of the executable itself. It should be embedded statically into the executable (so that can be seen from hex editor), rather than computed on the fly.
如果你对这篇内容有疑问,欢迎到本站社区发帖提问 参与讨论,获取更多帮助,或者扫码二维码加入 Web 技术交流群。

绑定邮箱获取回复消息
由于您还没有绑定你的真实邮箱,如果其他用户或者作者回复了您的评论,将不能在第一时间通知您!

发布评论
评论(4)
正如@Shi & @matthewdaniel 已经说过,这不能直接完成。
然而,有几种解决方法是可能的:
As both @Shi & @matthewdaniel have already said, this can't be done directly.
However a couple of workarounds are possible:
这是不可能的。
如果将 md5 哈希值输入到二进制文件中,则二进制文件将发生变化,因此 md5 哈希值也会发生变化。如果您创建一个新的,并尝试将其添加到二进制文件中,则二进制文件将再次更改。
因此最好的方法是将哈希值放入文件中,然后读取该文件并显示其内容。
另一种方法是创建二进制文件的 md5 哈希值,然后将其附加到可执行文件。为了获取该值,您读取二进制文件的最后 32 个字节并将其显示为 md5。当然,如果您创建完整可执行文件的哈希值,它将与哈希值不匹配 - 您必须创建可执行文件的哈希值(不包括最后 32 个字节)。
如果以原始格式(基数 256 而不是基数 16)存储 128 位 md5 哈希值,则只需要 16 字节。
This is not possible.
If you enter the md5 hash into the binary, the binary will change, so the md5 hash changes as well. If you create a new one, and try to add it to the binary, the binary will change again.
So best is to put the hash into a file, and read that file and display its content.
Another way could be to create the md5 hash of the binary, and then append it to the executable. In order to fetch the value, you read the last 32 byte of the binary and display it as md5. Of course, if you create a hash of the complete executable, it won't match the hash - you have to create the hash of the executable excluding the last 32 byte.
If you store the 128 bit md5 hash in a raw format (base 256 instead of base 16), you only need 16 byte.
一旦您将 md5 添加到文件中,该文件将具有不同的 md5。无法获取文件本身的 md5。
As soon as you add the md5 to the file the file will have a different md5. There is no way to get the md5 in the file itself.
典型的方法是签名。签名是由公钥/私钥进一步签名的哈希值。应用程序可以使用公钥来验证其中包含的哈希值。
但是,这需要与可执行文件分开。正如其他答案所述,不可能用一个文件来做到这一点。您可以合并签名和二进制文件,并提供使用工具将它们分开以计算验证的说明。
但是,这并不能阻止针对应用程序的内存中攻击。即,缓冲区溢出,攻击者可以在内存中重写代码。
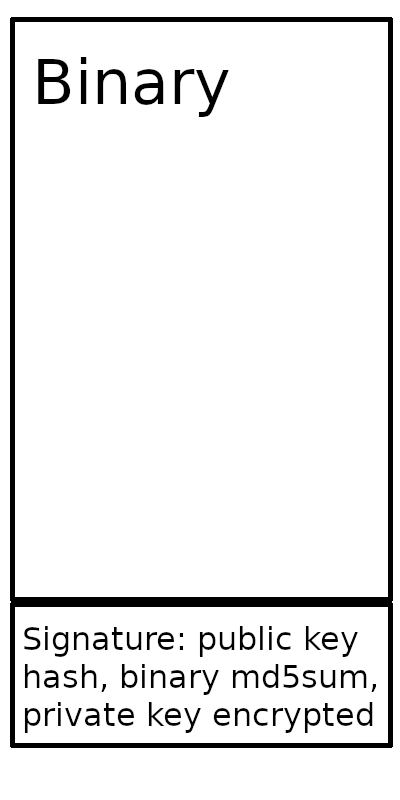
您可能不需要公钥的哈希值。您需要加密二进制文件的哈希值,使其无法更改。您可以使用公钥的哈希值来验证对用户的指令等。公钥的分发和验证指令不能捆绑在一起。否则,攻击者可以使用备用密钥对重新创建。包含公钥的散列可以防止针对指令的某些其他攻击。即,签名具有一些验证,以证明所公布的公钥与二进制文件的签名相匹配。
使用既定方法可能更好,因为用户可以使用替代工具来验证完整性。此外,这只使得公钥需要通过其他渠道分发。
参考: 使用 OpenSSL 进行数字签名
上面修复了另一种攻击。鉴于您所说的是可能的,什么会阻止其他人做同样的事情,但使用特洛伊木马二进制文件。公钥的分发是对来源(合法开发者)的认证。其他答案都没有解决这个问题。
The typical method is a signature. A signature is a hash that is further signed by a public/private key. The application can use the public key to verify the hash contained within.
However, this needs to be separate from the executable. As the other answers state, it is impossible to do this with one file. You can merge the signature and the binary and provide instructions to use tools to separate them to compute the verification.
However, this does not stop in-memory attacks against the application. Ie, you have a buffer overflow and an attacker can re-write code in memory.

You might not need the hash of the public key. You need to encrypt the hash of the binary so it can not be altered. You might use the hash of the public key to verify instructions to user, etc. The distribution of the public key and verification instruction can not be bundled. Otherwise an attacker can just re-create with an alternate key pair. Including the hash of the public key can prevent some other attack against instruction. Ie, the signature has some verification that the advertised public key is matching what the binary was signed with.
Using established methods is probably better as users can have alternate tools to verify the integrity. Also, this only makes the public key needed to distribute through some other channel.
Reference: Digital signature with OpenSSL
The above fixes another attack. Given that what you said was possible, what would stop someone else from doing the same thing, but with a trojan horse binary. Distribution of the public key is an authentication of the source (legitimate developer). None of the other answers addressed this.