PHP中的SQL注入MySql
我必须做一个关于如何进行 MySQL 注入以及如何保护我们免受它们攻击的小演示。我已经确切知道如何保护我们的应用程序,但我对 SQL 注入有一些疑问。
A 创建了一个简单的虚拟网站用于演示,我在其中添加了一个搜索字段。此搜索字段不受保护,因此容易受到 SQL 注入的影响。
我已经做了一些例子,比如如何检索数据库上的一些全局信息(版本、当前用户、数据库名称),插入 " 'UNION SELECT [MyInteresstingFields] From [mytable]; --" ,但我的问题是:
下一步是什么?数据库可以修改吗?如何?我不明白,因为 mysql_query(这是一个使用 cakePhp 的 php 网站)只运行一个请求,那么如何改变 SELECT 请求来对数据库进行更改?(例如插入、编辑或其他任何操作,没关系,它是只是为了向他们展示结果)。
I've to make a small demonstration about how to make a MySQL Injection and how to protect us against them. I already know exactly how to protect our application for then, but I've some question about SQL injection.
A created a simple dummy website for the demonstration, on which I've added a search field. This search field isn't protected so subject to SQL injection.
I already made some example, like how to retrieve some global info on the database(version, current user, database name), inserting a " 'UNION SELECT [MyInteresstingFields] From [mytable]; --", but my question is:
What is the next step? Is it possible to alter the database? How? I don't see, because mysql_query(it's a php website using cakePhp) only runs one request, so how alter a SELECT request to make a change in the database?(e.g. insert, edit or anything else, doesn't matter, it's only to show them what can be the result).
如果你对这篇内容有疑问,欢迎到本站社区发帖提问 参与讨论,获取更多帮助,或者扫码二维码加入 Web 技术交流群。

绑定邮箱获取回复消息
由于您还没有绑定你的真实邮箱,如果其他用户或者作者回复了您的评论,将不能在第一时间通知您!

发布评论
评论(4)
通常,您将使用注入来收集管理员密码(或通过密码重置页面通过电子邮件发送的令牌),然后登录到管理部分并从那里执行操作。
Usually you will use the injection to collect admin passwords (or the token emailed via a password reset page), then login to the admin part and do the stuff from there.
这里是测试sql注入的教程
Sql注入教程
Here is the tutorial for testing the sql injection
Sql Injection Tutorial
mysql_query()仅执行一个查询,其目的是在您容易受到 SQL 注入攻击时保护您免受 alter/drop/insert/update/delete 语句的影响。但是,如果易受攻击的代码是INSERT、UPDATE或DELETE语句怎么办?然后,您可以删除所有行,修改 where,或者您可以添加另一行,如果您可以将'), ()' 添加到查询,或者您可以更新 access_level用户的,即使原始查询仅更新密码(如果密码字段未转义,并且用户输入", access_level=1作为密码mysql_query()executes only one query exactly for the purpose to protect you from alter/drop/insert/update/delete statements if you are vulnerable to sql injection. But what if the vulnerable code isINSERT,UPDATEorDELETEstatement? Then you can delete all rows, modifying the where, or maybe you could add another row, if you can add'), (<values>)'to the query, or you can update the access_level of the user, even if the original query updates only the password (if the password field is not escaped, and user enters", access_level=1for the password如果您的目的是在没有管理权限的情况下通过 SQL 注入更改 MySQL 中的数据,那么您**不能**。尽管使用 SQL Server 是可能的。 。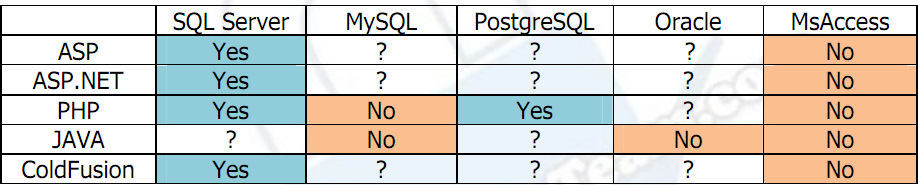
if your intention is to alter data in MySQL with sql injection without administrative privileges then you **can't ** . Although it's possible with SQL server . .