防止复制保护规避
任何访问种子跟踪器的人肯定会发现大量“破解”程序,从简单的共享软件到价值数千美元的软件套件。 似乎只要程序不依赖于远程服务(例如MMORPG),任何内置的复制保护或用户身份验证都是无用的。
是否实际上无法阻止破解者绕过复制保护? 为什么?
Anyone visiting a torrent tracker is sure to find droves of "cracked" programs ranging from simple shareware to software suites costing thousands of dollars. It seems that as long as the program does not rely on a remote service (e.g. an MMORPG) that any built-in copy protection or user authentication is useless.
Is it effectively not possible to prevent a cracker from circumventing the copy protection? Why?
如果你对这篇内容有疑问,欢迎到本站社区发帖提问 参与讨论,获取更多帮助,或者扫码二维码加入 Web 技术交流群。

绑定邮箱获取回复消息
由于您还没有绑定你的真实邮箱,如果其他用户或者作者回复了您的评论,将不能在第一时间通知您!

发布评论
评论(18)
不,实际上不可能阻止它。 你可以让它变得极其困难——一些星际力量版本显然做到了这一点,但代价是严重激怒了一些“用户”(受害者可能更准确)。
你的代码在他们的系统上运行,他们可以用它做任何他们想做的事情。 连接调试器、修改内存等等。 就是这样。
Spore 似乎是一个优雅的例子,说明在这个方向上的严厉努力不仅完全未能阻止它在 P2P 网络等周围共享,而且还显着 损害了产品的形象,而且几乎肯定损害了销售。
另外值得注意的是,用户可能需要破解复制保护以供自己使用; 我记得几年前在我的笔记本电脑上玩《暗黑破坏神》,当时它没有内置光驱。 于是我就加入了一个无 CD 的破解版,然后在长途飞机上享受了几个小时的娱乐。 强制进行这种检查,从而让用户绕过它是最愚蠢的错误。
No, it's not really possible to prevent it. You can make it extremely difficult - some Starforce versions apparently accomplished that, at the expense of seriously pissing off a number of "users" (victims might be more accurate).
Your code is running on their system and they can do whatever they want with it. Attach a debugger, modify memory, whatever. That's just how it is.
Spore appears to be an elegant example of where draconian efforts in this direction have not only totally failed to prevent it from being shared around P2P networks etc, but has significantly harmed the image of the product and almost certainly the sales.
Also worth noting that users may need to crack copy protection for their own use; I recall playing Diablo on my laptop some years back, which had no internal optical drive. So I dropped in a no-cd crack, and was then entertained for several hours on a long plane flight. Forcing that kind of check, and hence users to work around it is a misfeature of the stupidest kind.
如果不破坏您的产品,就不可能阻止它。 证据:
假设:您试图阻止黑客攻击/窃取的人将不可避免地比您的大部分市场在技术上更加复杂。
鉴于:您的产品将被某些公众使用。
鉴于:使用您的产品需要在某种程度上访问其数据。
因此,您必须以足够的方式向公众发布加密密钥/复制保护方法/程序数据,以使数据以其可用/未加密的形式被看到。
因此,您以某种方式让盗版者可以访问您的数据。
因此,与合法受众相比,黑客更容易访问您的数据。
因此,任何超过最简单保护方法的做法最终都会像对待盗版者一样对待您的合法受众并疏远他们
或者简而言之,最终用户的看法是:
It is impossible to stop it without breaking your product. The proof:
Given: The people you are trying to prevent from hacking/stealing will inevitably be much more technically sophisticated than a large portion of your market.
Given: Your product will be used by some members of the public.
Given: Using your product requires access to it's data on some level.
Therefore, You have to released you encrypt-key/copy protection method/program data to the public in enough of a fashion that the data has been seen in it's useable/unencrypted form.
Therefore, you have in some fashion made your data accessible to pirates.
Therefore, your data will be more easily accessible to the hackers than your legitimate audience.
Therefore, ANYTHING past the most simplistic protection method will end up treating your legitimate audience like pirates and alienating them
Or in short, the way the end user sees it:

因为这是针对有思想的对手的固定防御。
多少年前军事理论家就把这个人打死了?
Because it's a fixed defense against a thinking opponent.
The military theorists beat this one to death how many millennia ago ?
复制保护就像安全性一样——不可能达到 100% 完美,但您可以添加层数,使其逐渐更难以破解。
大多数应用程序都会在某些时候(自己)问“许可证有效吗?” 黑客只需找到该点并更改编译的代码以返回“是”。 或者,破解者可以使用暴力尝试不同的许可证密钥,直到其中一个有效。 还有社会因素——一旦有人购买了该工具,他们可能会在互联网上发布有效的许可证代码。
因此,代码混淆使得找到要更改的代码变得更加困难(但并非不可能)。 二进制文件的数字签名使得更改代码变得更加困难,但仍然不是不可能。 可以使用带有大量纠错位的长许可证代码来对抗暴力方法。 可以通过要求姓名、电子邮件和电话号码作为许可证代码本身的一部分来缓解社交攻击。 我用过这个方法,效果很好。
祝你好运!
Copy-protection is like security -- it's impossible to achieve 100% perfection but you can add layers that make it successively more difficult to crack.
Most applications have some point where they ask (themselves), "Is the license valid?" The hacker just needs to find that point and alter the compiled code to return "yes." Alternatively, crackers can use brute-force to try different license keys until one works. There's also social factors -- once one person buys the tool they might post a valid license code on the Internet.
So, code obfuscation makes it more difficult (but not impossible) to find the code to alter. Digital signing of the binaries makes it more difficult to change the code, but still not impossible. Brute-force methods can be combated with long license codes with lots of error-correction bits. Social attacks can be mitigated by requiring a name, email, and phone number that is part of the license code itself. I've used that method to great effect.
Good luck!
抱歉打扰了一个古老的话题,但这就是我们的谋生方式,而且我们真的很擅长。 这就是我们所做的一切。 所以这里的一些信息是错误的,我想澄清一下。
理论上,不可破解的保护不仅是可能的,而且也是我们所销售的。 主要复制保护供应商(包括我们)遵循的基本模型是使用 exe 和 dll 的加密以及运行时解密的密钥。
共有三个组成部分:
非常强大的加密:我们使用 AES 128 位加密,可以有效抵御暴力攻击。 有一天,当量子计算机变得普遍时,也许有可能破解它,但假设你会破解这种强度加密来复制软件而不是国家机密,这是不合理的。
安全密钥存储:如果破解者能够获得加密密钥,那么您就完蛋了。 保证密钥不被盗的唯一方法是将其存储在安全设备上。 我们使用加密狗(它有多种版本,但操作系统总是将其视为可移动闪存驱动器)。 加密狗将密钥存储在智能卡芯片上,该芯片针对 DPA 等侧通道攻击进行了强化。 密钥的生成与多个不确定性和动态因素相关,因此单个密钥/主破解是不可能的。 密钥存储和计算机上的运行时之间的通信也经过加密,因此可以阻止中间人攻击。
调试器检测:基本上,您希望阻止破解者拍摄内存快照(解密后)并从中生成可执行文件。 我们为防止这种情况所做的一些事情是秘密的,但一般来说,我们允许调试器检测并在调试器存在时锁定许可证(这是一个可选设置)。 我们也永远不会完全解密内存中的整个程序,因此您永远无法通过“窃取”内存来获取所有代码。
我们有一名全职密码学家,他几乎可以破解任何人的保护系统。 他把所有的时间都花在研究如何破解软件上,这样我们就可以阻止它。 因此,您不会认为这只是我们所做的事情的廉价托儿,我们并不是独一无二的:SafeNet 和 Arxan Technologies 等其他公司也可以提供一些非常强大的保护。
许多纯软件或混淆方案很容易破解,因为破解者只能识别程序入口点并围绕任何许可证检查或 ISV 为防止盗版而放入的其他内容进行分支。 有些人即使拥有加密狗也会在找不到许可证时弹出一个对话框 - 在该错误上设置断点将为破解者在汇编代码中提供一个很好的位置来进行修补。 同样,这需要未加密的机器代码可用——如果您对 .exe 进行强加密,则无法获得这些代码。
最后一件事:我认为我们的独特之处在于我们举办了几次公开竞赛,我们向人们提供了一个系统并邀请他们破解它。 我们已经获得了一些相当丰厚的现金奖励,但还没有人破解我们的系统。 如果ISV采用了我们的系统并错误地实施了它,这就像在你的前门上放一把大挂锁,用木螺丝固定在廉价的搭扣上一样——很容易被绕过。 但如果您按照我们的建议使用我们的工具,我们相信您的软件无法被破解。
HTH。
Sorry to bust in on an ancient thread, but this is what we do for a living and we're really really good at it. It's all we do. So some of the information here is wrong and I want to set the record straight.
Theoretically uncrackable protection is not only possible it's what we sell. The basic model the major copy protection vendors (including us) follow is to use encryption of the exe and dlls and a secret key to decrypt at runtime.
There are three components:
Very strong encryption: we use AES 128-bit encryption which is effectively immune to a brute force attack. Some day when quantum computers are common it might be possible to break it but it's unreasonable to assume you will crack this strength encryption to copy software as opposed to national secrets.
Secure key storage: if a cracker can get the key to the encryption, you're hosed. The only way to GUARANTEE a key can't be stolen is to store it on a secure device. We use a dongle (it comes in many flavors but the OS always just sees it as a removable flash drive). The dongle stores the key on a smart card chip which is hardened against side channel attacks like DPA. The key generation is tied to multiple factors which are non-deterministic and dynamic so no single key/master crack is possible. The communication between the key storage and the runtime on the computer is also encrypted so a man-in-the-middle attack is thwarted.
Debugger detection: Basically you want to stop a cracker from taking a snapshot of memory (after decryption) and making an executable out of that. Some of the stuff we do to prevent this is secret, but in general we allow for debugger detection and lock the license when a debugger is present (this is an optional setting). We also never completely decrypt the entire program in memory so you can never get all the code by "stealing" memory.
We have a full time cryptologist who can crack just about anybody's protection system. He spends all his time studying how to crack software so we can prevent it. So you don't think this is just a cheap shill for what we do, we're not unique: other companies such as SafeNet and Arxan Technologies can do some very strong protection as well.
A lot of software-only or obfuscation schemes are easy to crack since the cracker can just identify the program entry point and branch around any any license checking or other stuff the ISV has put in to try to prevent piracy. Some people even with dongles will throw up a dialog when the license isn't found--setting a breakpoint on that error will give the cracker a nice place in the assembly code to do a patch. Again, this requires unencrypted machine code to be available--something you don't get if you do strong encryption of the .exe.
One last thing: I think we're unique in that we've had several open contests where we provided a system to people and invited them to crack it. We've had some pretty hefty cash prizes but no one has yet cracked our system. If an ISV takes our system and implements it incorrectly it's no different from putting a great padlock on your front door attached to a cheap hasp with wood screws--easy to circumvent. But if you use our tools as we suggest we believe your software cannot be cracked.
HTH.
安全性和复制保护之间的区别在于,通过安全性,您可以保护资产免受攻击者的侵害,同时允许授权用户访问。 通过复制保护,攻击者和授权用户是同一个人。 这使得完美的复制保护变得不可能。
The difference between security and copy-protection is that with security, you are protecting an asset from an attacker while allowing access by an authorized user. With copy protection, the attacker and the authorized user are the same person. That makes perfect copy protection impossible.
我认为,只要有足够的时间,潜在的破解者就可以绕过任何复制保护,甚至是使用远程服务器回调的复制保护。 所需要做的就是通过一个盒子重定向所有传出流量,该盒子将过滤这些请求,并以适当的消息进行响应。
在足够长的时间线上,复制保护系统的存活率为0。只要有足够的时间和知识,一切都是可以逆向工程的。
也许您应该关注如何通过真实的、注册的、未破解的版本使您的软件更具吸引力。 优质的客户服务、注册福利等奖励合法用户。
I think given enough time a would-be cracker can circumvent any copy-protection, even ones using callbacks to remote servers. All it takes is redirecting all outgoing traffic through a box that will filter those requests, and respond with the appropriate messages.
On a long enough timeline, the survival rate of copy protection systems is 0. Everything is reverse-engineerable with enough time and knowledge.
Perhaps you should focus on ways of making your software be more attractive with real, registered, uncracked versions. Superior customer service, perks for registration, etc. reward legitimate users.
基本上,历史告诉我们,通过复制保护最多可以买到一点时间。 从根本上说,既然您希望某人以某种方式查看某些数据,那么就有一种方法可以获取该数据。 因为有人可以利用这种方式来获取数据。
与此相关的任何复制保护或加密唯一能做的就是使获取某些内容变得非常困难。 如果一个人有足够的动力,总有办法用蛮力的方式来解决问题。
但更重要的是,在计算机软件领域,我们有大量的工具可以让我们了解事情是如何工作的,一旦您掌握了复制保护如何工作的方法,那么获得您想要的东西就变得非常简单。
另一个问题是,复制保护在很大程度上只会让为您的软件付费的用户感到沮丧。 看看他们不关心的开源模型,有些人通过鼓励人们复制他们的软件赚了很多钱。
Basically history has shown us the most you can buy with copy protection is a little time. Fundamentally since there is data you want someone to see one way, there is a way to get to that data. Since there is a way someone can exploit that way to get to the data.
The only thing that any copy protection or encryption for that matter can do is make it very hard to get at something. If someone is motivated enough there is always the brute force way of getting around things.
But more importantly, in the computer software space we have tons of tools that let us see how things are working, and once you get the method of how the copy protection works then its a very simple matter to get what you want.
The other issue is that copy protection for the most part just frustrates your users who are paying for your software. Take a look at the open source model they don't bother and some folks are making a ton of money encouraging people to copy their software.
“试图让位不可复制就像试图让水不湿一样。”——Bruce Schneier
复制保护和其他形式的数字限制管理本质上是容易被破坏的,因为不可能制作出一系列的数据流。位对计算机可见,同时防止计算机复制它们。 这是做不到的。
正如其他人指出的那样,复制保护只会惩罚合法客户。 我不想玩《孢子》,但如果玩的话,我可能会购买它,然后安装破解版,因为它实际上是一个更好的产品,因为它没有破坏系统的 SecuROM 或剥夺财产的激活方案。
"Trying to make bits uncopyable is like trying to make water not wet." -- Bruce Schneier
Copy protection and other forms of digital restrictions management are inherently breakable, because it is not possible to make a stream of bits visible to a computer while simultaneously preventing that computer from copying them. It just can't be done.
As others have pointed out, copy protection only serves to punish legitimate customers. I have no desire to play Spore, but if I did, I'd likely buy it but then install the cracked version because it's actually a better product for its lack of the system-damaging SecuROM or property-depriving activation scheme.
}} 为什么?
您可以购买世界上最昂贵的保险箱,并用它来保护某些东西。 一旦你放弃了打开保险箱的密码,你就失去了安全感。
软件也是如此,如果你想让人们使用你的产品,你必须赋予他们打开众所周知的保险箱并访问内容的能力,混淆打开锁的方法没有帮助。 您已授予他们打开它的能力。
}} Why?
You can buy the most expensive safe in the world, and use it to to protect something. Once you give away the combination to open the safe, you have lost your security.
The same is true for software, if you want people to use your product you must given them the ability to open the proverbial safe and access the contents, obfuscating the method to open the lock doesn't help. You have granted them the ability to open it.
您可以信任您的客户/用户,也可以浪费大量时间和资源试图击败他们,而不是提供他们想要付费的功能。
只是不值得打扰。 真的。 如果你不保护你的软件,即使它很好,毫无疑问有人会盗版它。 当然,门槛会很低。 但是,您不打扰所节省的时间将是您可以投资于产品、营销、客户关系等的时间,从而建立长期的客户群。
如果您确实花时间保护您的产品而不是开发它,那么盗版肯定会减少。 但现在你的竞争对手可能能够开发你没有时间开发的功能,而且你很可能最终销量减少,即使是在短期内。
You can either trust your customers/users, or you can waste inordinate amounts of time and resource trying to defeat them instead of providing the features they want to pay for.
It just doesn't pay to bother. Really. If you don't protect your software, and it's good, undoubtedly someone will pirate it. The barrier will be low, of course. But the time you save from not bothering will be time you can invest in your product, marketing, customer relationships, etc., building your customer base for the long term.
If you do spend the time on protecting your product instead of developing it, you'll definitely reduce piracy. But now your competitors may be able to develop features that you didn't have time for, and you may very well end up selling less, even in the short term.
正如其他人指出的那样,您很容易让真实合法的用户感到沮丧,而不是让骗子感到沮丧。 当您开发规避技术时,请始终牢记您的付费用户。
如果你的软件被需要,你就没有希望对抗那群无聊的 17 岁年轻人。 :)
As others point out, you can easily end up frustrating real and legitimate users more than you frustrate the crooks. Always keep your paying users in mind when you develop a circumvention technique.
If your software is wanted, you have no hope against the army of bored 17 year old's. :)
在个人复制/非商业版权侵权的情况下,关键因素似乎是项目的价格与复制的难易程度之间的关系。 您可以增加复制它的难度,但正如之前的一些答案所强调的那样,收益递减。 另一种策略是降低价格,直到通过 BitTorrent 下载它比简单地购买更麻烦。
实际上有很多成功的例子,作者找到了定价的最佳点,这无疑为自己带来了巨额利润。 试图追求100%防未经授权的复制是注定失败的,你只需要获得一大批愿意付费的客户,而不是非法下载。 盗版软件变得便宜的原因也使得软件发布变得便宜。
In the case of personal copying/non-commercial copyright infringement, the key factor would appear to be the relationship between the price of the item and the ease of copying it. You can increase the difficulty to copy it, but with diminishing returns as highlighted by some of the previous answers. The other tack to take would be to lower the price until even the effort to download it via bittorrent is more cumbersome than simply buying it.
There are actually many successful examples where an author has found a sweet spot of pricing that has certainly resulted in a large profit for themselves. Trying to chase a 100% unauthorized copy prevention is a lost cause, you only need to get a large group of customers willing to pay instead of downloading illegaly. The very thing that makes pirating softweare inexpensive is also what makes it inexpensive to publish software.
有一个简单的方法,我很惊讶你在上面的答案中没有这么说。
将复制保护移至安全区域(了解安全实验室中的服务器)。
您的服务器将从客户端接收随机数(检查该数字以前没有使用过),用客户端的号码和您的私钥加密一些不断发展的二进制代码/计算结果并将其发送回来。
任何黑客都无法规避这一点,因为他们无权访问您的服务器代码。
我所描述的基本上是 Web 服务,而不是 SSL,这是当今大多数公司所采用的方式。
缺点:在您完成加密代码期间,竞争对手将开发相同功能产品的离线版本。
There's an easy way, I'm amazed you haven't said so in the answers above.
Move the copy protection to a secured area (understand your server in your secure lab).
Your server will receive random number from clients (check that the number wasn't used before), encrypt some ever evolving binary code / computation results with clients' number and your private key and send it back.
No hacker can circumvent this since they don't have access to your server code.
What I'm describing is basically webservice other SSL, that's where most company goes nowadays.
Cons: A competitor will develop an offline version of the same featured product during the time you finish your crypto code.
关于不需要网络的保护:
根据流传的注释,破解一个流行应用程序花了两年时间,该应用程序使用与约翰的回答中描述的类似方案。 (定制硬件加密狗保护)
另一种不涉及加密狗的方案是“扩展保护”。 我刚刚创造了这个,但它的工作原理是这样的:有一个应用程序可以保存用户数据,并且用户可以从第三方购买扩展等。 当用户加载数据或使用新的扩展时,扩展和保存的数据还包含执行检查的代码。 当然,这些检查也受到校验和检查的保护。 它在纸面上不像其他方案那么安全,但实际上这个应用程序一直处于半破解状态,因此尽管已被破解,但它主要充当试用版,因为破解总是会错过一些检查,并且必须修补这些扩展出色地。
关键是,虽然这些可以被破解,但如果有足够多的软件供应商使用此类方案,这将使软件界中愿意致力于这些方案的少数人过度劳累。 如果你计算一下,保护措施不必那么好,只要有足够多的供应商使用这些不断变化的自定义保护措施,它就会压倒破解者,软件场景就会在那里结束。 *
这种情况没有发生的唯一原因是发行商购买了他们在各处使用的单一保护,使其成为一个巨大的目标,就像 Windows 是恶意软件的目标一样,任何保护在多个应用程序中使用是一个更大的目标。 因此,每个人都需要进行自己的定制、独特的多层扩展保护。 如果最优秀的破解者需要几个月的时间来破解一个版本,那么每年发布的软件版本数量可能会下降到几十个版本。
现在我们来谈谈营销软件中的一些理论:
如果您认为warez 提供了有价值的营销价值,那么就应该在商业计划中考虑到这一点。 这可能需要一个非常非常(太)基本的精简版本,但仍然需要花费几美元来确保它被破解。 然后,您可以通过定期提供“从精简版廉价升级的限时升级”优惠和其他追加销售策略来吸引用户。 精简版实际上最多应该有一项值得购买的功能,否则就会非常糟糕。 价格大概应该<10美元。 完整版的升级价格可能是 10 美元精简版付费演示版的两倍。 例如。 如果完整版的价格是 80 美元,那么您可以以 40 美元的价格从精简版升级到完整版,或者看起来真的很划算。 当然,您应该避免向直接购买 80 美元版本的购买者透露这些特价商品。
至关重要的是,完整版的代码与精简版没有相似之处。 您可能希望精简版被盗用,而完整版要么需要大量时间来破解,要么在功能上具有网络依赖性,很难在本地模仿。 破解者可能更专注于破解,而不是尝试编码/复制应用程序在 Web 服务器上具有的部分功能。
* 附录:对于应用程序/游戏,场景可能会在这种不可能的理论情况下结束,对于音乐/电影等其他东西,在实践中,我会考虑让数字 dl 购买者能够便宜地获得额外的可收藏的实物物品或仅限在线的价值 - 许多人都是物品的收藏家(尤其是盗版者),如果这些物品比数字副本获得了足够令人满意的东西,他们可能会被吸引购买。
但要小心——有一种叫做“期望上升定律”的东西。 游戏示例:Ultima 4-6 标准盒中包含一张由布制成的地图,而《Skyrim》收藏版则包含一张由纸制成的地图。 期望值上升,有些人不会对纸质地图感到满意。 您希望保持产品或服务质量恒定,或者提前管理期望。 我认为,在考虑这些增值产品时,这一点至关重要,因为您希望它们的制造成本令人满意,但又不会变得越来越昂贵,并且不会变成看起来毫无价值的东西,从而违背了目的。
On protections that don't require network:
According to notes floated around it took two years to crack a popular application which used similar scheme as described in John's answer. (custom hardware dongle protection)
Another scheme which doesn't involve a dongle is "expansive protection". I coined this just now, but it works like this: There's an application which saves user data and for which the users can buy expansions and such from 3rd parties. When user loads the data or uses new expansion, the expansions and the saved data contains also code which performs checks. And of course these checks are also protected by checksum checks. It's not as secure on paper as the other scheme but in practise this application has been half-cracked all the time, so that it mostly functions as a trial despite being cracked as the cracks will always miss some checks and have to patch these expansions as well.
The key point is, while these can be cracked, if enough software vendors used such schemes, this would overwork the few people in the warescene who are willing to dedicate themselves to those. If you do the maths, the protections don't have to be even that great, as long as enough vendors used these custom protections that changed constantly, it would simply overwhelm the crackers and the warez scene would end then and there. *
The only reason this hasn't happened is because publishers buy a single protection that they use all over, making it a huge target just like Windows is target for malware, any protection used in more than single app is a bigger target. So everyone needs to be doing their own custom, unique multi-layered expansive protection. The amount of warez releases would drop to maybe dozen releases per year if it takes months to crack a single release by the very best crackers.
Now for some theorycrafting in marketing software:
If you believe that warez provides worthwhile marketing value, then that should be factored in the business plan. This could entail a very very (too) basic lite version that still cost few dollars to ensure it was cracked. Then you'd hook in the users with "limited time upgrade cheaply from the lite version" offers regularly and other upselling tactics. The lite version should really have at most one buy-worthy feature and otherwise be very crippled. The price should probably be <10 $. The full version should probably be twice as much as the upgrade price from the $10 lite pay-demo version. eg. If the full-version is $80, You'd offer upgrades from the lite version to full version for $40 or something that really seems like killer bargain. Of course you'd avoid revealing these bargains to purchasers who went direct for the $80 edition.
It would be critical that the full version shared no similarity in code to the lite version. You'd intend that the lite-version gets warezed and the full-version will either be time intensive to crack or have network dependency in functionality that will be hard to mimic locally. Crackers are probably more specialized in cracking than trying to code up/replicate parts of functionality that the application has on the web server.
* addendum: for apps/games the scene might end in such unlikely and theoretical circumstance, for other things like music/movies and in practise, I'd look at making it cheap for digital dl buyers to get additional collectible physical items or online-only value - many people are collectors of stuff (especially the pirates) and they could be enticed into buying if it gains something desirable enough over just a digital copy.
Beware though - There's something called "the law of rising expectations". Example from games: Ultima 4-6 standard box included a map made of cloth, and Skyrim Collectors edition has a map made of paper. Expectations had risen and some people aren't going to be happy with a paper map. You want to either keep quality of produce or service constant or manage expectations ahead of time. I believe this is critical when considering these value-add things as you want them to be desirably but not increasingly expensive to make and not turn into something that seems so worthless that it defeats the purpose.
在这种情况下,高质量的软件是一件坏事,因为如果没有人知道你的软件,那么他们就不会花时间尝试破解它,另一方面,像 Adobe 的 Master Collection CS3 这样的东西,在发布几天后就可用了。
因此,这个故事的寓意是,如果您不想让别人窃取您的软件,那么有一个选择:不要编写任何值得窃取的内容。
This is one occasion where quality software is a bad thing, because if no one whats your software then they will not spend time trying to crack it, on the other hand things like Adobe's Master Collection CS3, were available just days after release.
So the moral of this story is if you don't want someone to steal your software there is one option: don't write anything worth stealing.
我认为有人会想出一种动态人工智能方法来击败当前所有标准的复制保护方法; 哎呀,我肯定很乐意因为解决这个问题而获得报酬。 一旦他们到达那里,就会开发出新的方法,但这会减慢速度。
社会阻止软件盗窃的第二个最佳方法是严厉惩罚并执行处罚。
最好的办法就是扭转道德的颓势,从而提高社会的诚信水平。
I think someone will come up with a dynamic AI way of defeating all the currently standard methods of copy protection; heck, I'd sure love to get paid to work on that problem. Once they get there then new methods will be developed, but it'll slow things down.
The second best way for society to stop theft of software, is to penalize it heavily, and enforce the penalties.
The best way is to reverse the moral decline, and thereby increase the level of integrity in society.
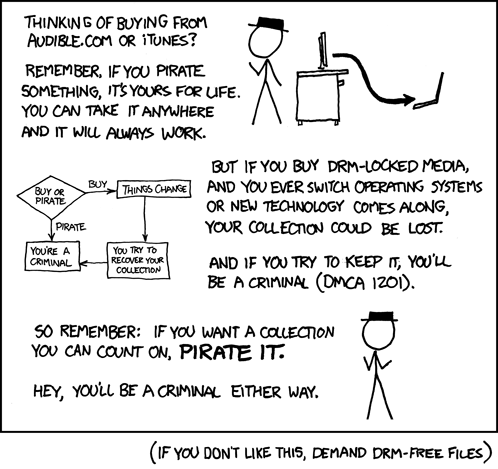
如果我听说过的话,那就是失败的原因……当然,这并不意味着你不应该尝试。
就我个人而言,我喜欢 Penny Arcade 的看法:“带有字面量的循环论证稻草人”替代文本 http://sonicloft.net/im/52
A lost cause if ever I heard one... of course that doesn't mean you shouldn't try.
Personally, I like Penny Arcade's take on it: "A Cyclical Argument With A Literal Strawman"alt text http://sonicloft.net/im/52