- About the Author
- About the Technical Editor
- Credits
- Acknowledgments
- Foreword
- Introduction
- CHAPTER 1 Fundamental Networking and Security Tools
- CHAPTER 2 Troubleshooting Microsoft Windows
- CHAPTER 3 Nmap—The Network Mapper
- CHAPTER 4 Vulnerability Management
- CHAPTER 5 Monitoring with OSSEC
- CHAPTER 6 Protecting Wireless Communication
- CHAPTER 7 Wireshark
- CHAPTER 8 Access Management
- CHAPTER 9 Managing Logs
- CHAPTER 10 Metasploit
- CHAPTER 11 Web Application Security
- CHAPTER 12 Patch and Configuration Management
- CHAPTER 13 Securing OSI Layer 8
- CHAPTER 14 Kali Linux
- CHAPTER 15 CISv7 Controls and Best Practices
CIS Basic Controls—The Top Six
I recommend that you go to the SANS website, www.sans.org , and look for conferences that are happening near you. In the evenings, they will have mini‐sessions free to the public, usually about an hour long each, of interesting security topics taught by the certified SANS instructors. Sometimes, if you're lucky, they will have an assortment and up to three or four in one evening. In the dozens of sessions I've attended, the one that stands out the most is the one Eric Conrad did a couple years ago in Orlando, Florida. He talked about the top six CIS controls. He said that while he was consulting for a governmental organization on another continent, implementing the top six controls negated about 80 percent of the problems resulting in more security and less likelihood of a breach.
The top six CISv7 basic controls are as follows:
- Inventory and Control of Hardware Assets
- Inventory and Control of Software Assets
- Continuous Vulnerability Management
- Controlled Use of Administrative Privileges
- Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
- Maintenance, Monitoring, and Analysis of Audit Logs
If you read about the major breaches in the last five years, most of them could have been avoided if the organization had subscribed to and executed these six controls. The CISv7 controls have cross‐compatibility or directly map to other cyber compliance and security standards like NIST 800‐53, PCI DSS, and HIPAA. This translates to other organizations using these suggestions as regulations to aid in their respective compliance. The NIST Cybersecurity Framework is another tool that organizations use to organize and strengthen their security posture using the CIS top controls as their baseline for several of their best practices. Let's look at these in more detail.
Inventory and Control of Hardware Assets
One of my favorite sayings in class is that “you cannot protect what you don't know you have.” This control specifically addresses the need to know what is connected to your network. You must develop policy and procedures around maintaining an accurate inventory. It can be rather tedious, but it is critical. If you do it right, it reduces loss risks. You must know what is on your network and who the system belongs to and use that data to prevent anyone unauthorized from accessing the network.
Creating a system inventory is a common task for system and network administrators. An open source security audit tool Nmap or Zenmap has all the necessary features needed to run an ad hoc or automated inventory process. By simply scanning a network using the operating system identification ( ‐O ) command switch and possibly verbose output ( ‐v ) command switch, you can get a list of systems and their protocols. The inventory created provides information that is critical to system, application, and protocol management. The inventory will not include information such as how much memory the system has or how many processors there are. This type of hardware inventory requires either an SNMP agent on the system or a script running on the system to determine the hardware in the system.
What do all network‐connected devices have in common? They speak to each other using a logical address called IP addresses. Who manages IP addresses? Dynamic Host Configuration Protocol (DHCP) manages IP addresses. DHCP also generates logs. For DHCP‐enabled networks, deploying a mechanism to focus on combining system inventory with configuration management and network access control is a win‐win. The inventory management portion is usually based on some type of endpoint management software like System Center Configuration Manager (SCCM). SCCM is a Microsoft systems management software product for managing large groups of computers from servers to workstations to mobile devices. Do not forget IoT when you are coming up with a management policy of your hardware inventory.
If you are a Microsoft customer with an existing Microsoft enterprise agreement, you may already have an SCCM license. SCCM provides software distribution, operating system deployment, and network access as well as the CIS control hardware inventory. There are a couple of options when implementing at SCCM. There is a datacenter edition as well as a standard edition. Both editions include the following tools:
- Configuration Manager—for managing the deployment of applications and devices in an enterprise network
- Data Protection Manager—for performing backup and recovery for business continuance and disaster recovery
- Endpoint Protection—for managing anti‐malware and firewall security
- Operations Manager—for monitoring the health and performance of operating systems and hypervisors
- Orchestrator—for standardizing and automating processes for operational efficiency
- Service Manager—for change control and asset lifecycle management
- Virtual Machine Manager—for provisioning and managing resources used to create virtual machines
Inventory and Control of Software Assets
Taking an inventory and control of software installed on your assets is taking the first control to the next level. You should be able to see what software is on your systems, who installed it, and what its function is. You need this information to prevent software that is not authorized from being installed on endpoints. Some organizations see this as a very complicated, highly managed process, but there are several ways to do this efficiently and automatically.
Many of the methods used to implement the inventory of authorized and unauthorized software will also improve the implementation of other controls relating to network access, asset configuration, and system management. Administrator access and installation rights should not be granted for every user. I have worked for organizations where all employees, including the warehouse personnel and receptionist, had administrative rights on their computer and could download any application they wanted with no processes in place to protect the network. Limiting who can install software also limits who can install seemingly innocent applications or games that include malware, adware, and other unwanted code.
Once installation rights have been limited, the next stage is creating a list of unauthorized and authorized applications. This is called blacklisting and whitelisting. Blacklisted software should never be allowed on the network, and whitelisting is the software the organization needs to get the job done. This can be rolled out as an authorized software policy first and followed up with scanning, removal, and, then, central inventory control. The inventory management portion is usually based on a software inventory tool or endpoint management services such as SCCM or based on GPO and local policy controls on Windows.
AppLocker, natively in Windows 10 and Server, can help you control which apps and files users can run on their systems. AppLocker can define rules based on file attributes, assign a rule to a group or user, and create exceptions to rules. It also helps reduce what is seemingly complicated, like standardizing approved software configuration to disallowing unlicensed software or certain apps from running.
Aside from AppLocker, Microsoft allows Group Policy–based whitelisting for supported versions of Windows. These can be edited locally using secpol.msc unless you have the Home version of Windows. If your organization has a domain controller or Group Policy Objects, you can use the same process by accessing Software Restriction Policies (SRP). For more general‐purpose workstations, a number of client‐based solutions exist, including antivirus and endpoint protection suites that limit software from a central console, like Carbon Blacks Consolidated Endpoint Security.
You can use software inventory to collect information about files on client devices that already exist. It can be a specific file, files with a specific extension, or all files on the computer. Software inventory can also collect files from client devices and store them on the site server. SCCM is an option for this kind of mature process, especially if you have it in place for hardware management as well. All the machines in an SCCM environment will have an SCCM client agent installed on them. This helps a machine to be able to communicate with the SCCM servers to receive their respective packages. Packages contain the executable files and the command lines for an application to be installed. These packages are then replicated on distribution points. Distribution points are servers used to store the content of the packages for a particular region. Machines that are remotely located can locally download the application from a distribution point, rather than connecting all the way to the SCCM primary server.
A deployment of approved software is created by the SCCM administrator. With the help of the SCCM client agent installed on the end user's machine, it keeps checking for new policies or deployments. After software inventory is enabled, clients run a software inventory cycle. The client sends the information to a management point in the client's site. The management point then forwards the inventory information to the SCCM site server. This information is stored in the site database. When software inventory runs on a client device, the first report is a full inventory. In the next cycle, the reports contain only updated inventory information, giving you the most current information of what is on that system.
Continuous Vulnerability Management
Organizations today operate in a constant dynamic stream of new security information: software updates, patches, and security advisories. It is easy to become overwhelmed with the amount of cybersecurity threat advisories that bombard our inboxes daily. Being able to understand and manage vulnerabilities is a continuous activity and requires a significant amount of time and attention to do it well.
A big part of your assessment and remediation has to do with scanning and finding the vulnerabilities in the hardware and software you have the inventory of from CIS controls 1 and 2. By not proactively scanning for vulnerabilities and addressing discovered flaws, the likelihood of an organization's computer systems becoming compromised is high. Identifying and remediating vulnerabilities on a regular basis is also essential to a strong overall information security program. Depending on your organization's maturity, you may scan monthly or weekly. Some three‐letter‐agencies I have worked with scan for vulnerabilities every single night and patch every day. You have to create a process around remediation and ensure that the most mission‐critical assets with the most dangerous vulnerabilities get fixed first.
One of my favorite sites that I recommend you add to your RSS feed is www.us‐cert.gov/ncas/current‐activity . This web page by the United States Computer Emergency Readiness Team is regularly updated with the most frequent and high‐impact security incidents. Another site is https://nvd.nist.gov/vuln/search . Here you can search the vulnerability database for a product, vendor, or specific CVE. Finally, https://cve.mitre.org/ is an extremely valuable resource for a list of entries with each containing an identification number, a description, and a reference for every publicly known cybersecurity vulnerability. I normally check in with these sites once a week to see what is out there.
Controlled Use of Administrative Privileges
Have you noticed that the critical controls are following a logical progression? As you gradually improve your security posture, they layer on top of each other. Now that you know what you have and what's on those machines, including vulnerabilities, you need to control who has access to those machines.
One of my favorite penetration tester's story is of a targeted phishing campaign launched against a specific department where six people clicked the link in the email, and two of the six were logged into their administrators account when they clicked and were compromised in 22 seconds. Within hours, the entire network belonged to the pen tester. You have to control who has administrative privileges and even how those administrators use their credentials. When you are logged in as an admin, you should not be opening your email under any circumstances. That is what your user account is for.
Two very common attacks rely on privilege to execute. That is one reason CVSS actually measures if privilege is necessary for exploitability. The first type of an attack is like the one I described previously where a user with elevated credentials opens a malicious attachment. The other is the elevation of privilege when cracking a password for an administrator. If the password policy is weak or not enforced, the danger increases exponentially.
Educate your leadership and help create a robust security posture where you restrict admin privilege. Have your IT admins make a list of the tasks that they do on an average day. Check the tasks that require administrative credentials. Create an account for normal tasks that all users can do and use the admin account for only those tasks where it's necessary. If you have executives insisting that they need admin privileges, remind them that they are the ones that hackers are targeting.
Microsoft has guidance on implementing least privilege. For Linux, each sysadmin should have a separate account and enforce the use of sudo by disabling su . You should also change all default passwords on all assets in your environment as well as making sure that each password is as robust as possible. Use multifactor authentication and configure systems to issue an alert if an admin mistypes his or her password.
The most secure admin credentials I've personally used were on a military network. My password was at least 16 characters, uppercase, lowercase, special characters, and could not spell anything in Meriam Webster's dictionary. I also had a lockout policy of one mistyped password. I was logging into upwards of 40 to 80 machines multiple times a day. If I locked myself out, I was basically in limbo for the rest of the day because I had to call the help desk to have them reset my password, which could take hours. That might be a bit extreme for the average organization, but the fundamentals are the same. By using robust passwords, limited privilege accounts, and a lockout policy, you are making it more difficult for the attacker to compromise your account or steal important data.
Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
If you have ever opened a new laptop freshly imaged with an operating system, you have to know that the default configuration you're working on setting up is extremely vulnerable. There are open ports open and services running and default accounts preinstalled for ease of use and deployment, which are all exploitable. In Windows, for example, there are a couple things you should do immediately after taking it out of the box.
In Lab 15.1 , you'll be securing a Windows workstation.
Maintenance, Monitoring, and Analysis of Audit Logs
Without appropriate logging, an attacker's activity could go unnoticed, and evidence can be inconclusive. Regular log collection is vital to understanding a security incident during an investigation. Logs are useful for baselines, trends, and support. At a minimum, log events should include the following:
- Operating system events
- Startup/shutdown of the system
- Startup/shutdown of a service
- Network connection changes or failures
- Changes to, or attempts to change, system security settings and controls
- OS audit records
- Logon attempts (successful or unsuccessful)
- Functions performed
- Account changes, including creation and deletion
- Successful/failed use of privileged accounts
- Application account information
- Successful/failed application authentication attempts
- Use of application privileges
- Application operations
- Application startup/shutdown
- Application failures
- Major application configuration changes
One of my favorite resources for logging is on a site called Malware Archaeology.
https://www.malwarearchaeology.com/cheat‐sheets/
As you can see in Figure 15.10 , it has a variety for everything logging.
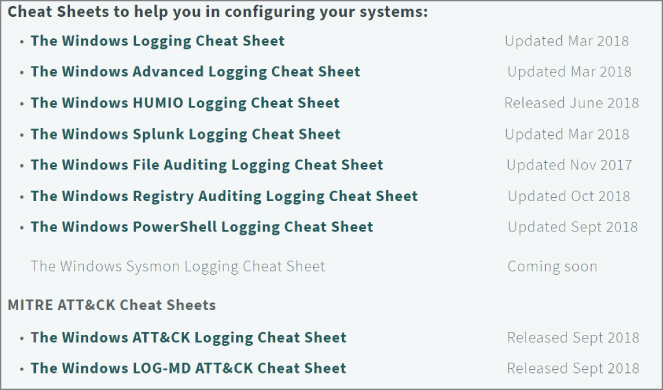
Figure 15.10 : Logging cheat sheets
After you have a strong foundation around the six basic CIS controls, it's time to add on the Foundational and Organizational controls. In Figure 15.11 , you see a list of the next layers of defense in depth that cybersecurity professionals put in place to keep organizations and users secure.

Figure 15.11 : CIS Controls
如果你对这篇内容有疑问,欢迎到本站社区发帖提问 参与讨论,获取更多帮助,或者扫码二维码加入 Web 技术交流群。

绑定邮箱获取回复消息
由于您还没有绑定你的真实邮箱,如果其他用户或者作者回复了您的评论,将不能在第一时间通知您!
发布评论